SSH Port Forwarding, also known as SSH Tunneling, is a method of securely forwarding network traffic through an SSH (Secure Shell) connection. It allows you to securely access resources on remote servers or networks that might otherwise be restricted or inaccessible.
SSH tunneling works by creating an encrypted SSH session between a client and a server, through which network traffic can be securely routed.
In practice, SSH port forwarding allows you to access network resources that are not directly reachable. For instance, if you are offsite and need to connect to a protected resource within a secure network, you can establish an SSH connection to an accessible machine within that network. This SSH connection then serves as a tunnel that forwards your requests to the protected resource.

Types of SSH Port Forwarding
Below is the mail types of port forwarding, each designed to meet specific needs. The main types include:
- Local port forwarding.
- Remote port forwarding.
- Dynamic port forwarding.
The sections below explain each type in detail.
1. Local Port Forwarding
- Purpose: Redirects traffic from a local machine to a remote server through an SSH connection.
- How it Works: You specify a local port that will forward traffic to a destination server and port on the remote side.
- Use Case: Accessing a resource (e.g., a database or web server) on a remote network that is not directly accessible from your local machine.
Example
ssh -L [local_port]:[destination_host]:[destination_port] [user]@[ssh_server]
ssh -L 8080:localhost:3306 user@remote-server
This forwards local port 8080 to the remote server’s port 3306 (e.g., MySQL).
Local Port Forwarding with PuTTY
PuTTY is a user-friendly SSH client for Windows. Configure local SSH tunneling by following these steps when you start the PuTTY application:
1. Enter the hostname or IP address and port number of the destination SSH server in the Sessions
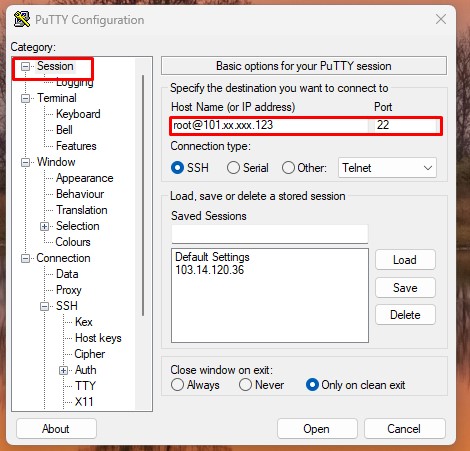
2. Use the Category list on the left to navigate to Connection > SSH > Tunnels.
3. Select Local to define the type of SSH port forward.
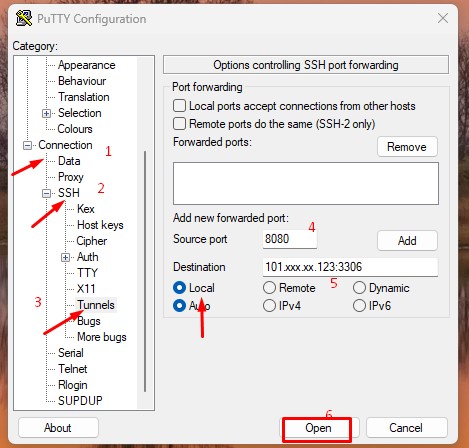
4. Enter your local port number in the Source port field.
5. Type the destination address and port number in the Destination field. Use the following format:
For example, Source port 8080 Destination:103.xxx.xx.123 :3306
6. Once you verify that the information you entered is correct, select Add.
7. The parameters for the connection are now all set. The Open option initiates the local SSH port-forward.
2.Remote Port Forwarding
- Purpose: Redirects traffic from the SSH server to a local machine through the SSH connection.
- How it Works: You specify a remote port that will forward traffic to a destination host and port on your local machine.
- Use Case: Exposing a local service (e.g., a web server running on your machine) to a remote client.
Command Example:
ssh -R [remote_port]:[destination_host]:[destination_port] [user]@[ssh_server]
Example:
ssh -R 8080:localhost:3000 user@remote-server
This forwards remote port 8080 to local port 3000 (e.g., a web server).
3. Dynamic Port Forwarding
- Purpose: Creates a SOCKS proxy server that can dynamically forward traffic to various destinations based on client requests.
- How it Works: You specify a local port to act as the SOCKS proxy. Applications that support SOCKS proxies (e.g., web browsers) can use this to tunnel traffic.
- Use Case: Accessing a variety of resources on a remote network or bypassing restrictions (e.g., bypassing a firewall).
Command Example:
ssh -D [local_port] [user]@[ssh_server]
Example:
ssh -D 1080 user@remote-server
This creates a SOCKS proxy on local port 1080.
How Does SSH Port Forwarding Work?
SSH port forwarding creates a secure tunnel between a local and a remote machine. This allows data to travel securely over an encrypted SSH connection. Once the SSH tunnel is established, the SSH client listens on a specified local port. It then forwards any traffic arriving at that port through the connection to the corresponding remote port.
This process makes the remote service accessible as if running on a local machine without exposing it to the internet. The SSH client and server manage data encryption and decryption to keep all transmitted information confidential.
Network traffic is directed to a specific port on the target computer. When that computer has an open port, it can receive data on that port. To avoid exposing your computer to the internet with open ports, your router acts as the primary defense against various probes and attacks.
Port forwarding allows legitimate traffic to pass through to your network by specifying rules on the router, such as the IP address and port. This directs data packets to the correct machine waiting for an SSH connection, ensuring secure access to remote services.
Advantages of SSH Port Forwarding
- Encryption: All traffic is encrypted, ensuring secure communication.
- Firewall Bypass: Useful for accessing resources behind firewalls or NAT.
- Versatility: Works with various protocols and applications, such as HTTP, database connections, and more.
Common Use Cases
- Securely accessing internal network resources (e.g., web servers or databases).
- Bypassing firewalls or network restrictions.
- Exposing local services to remote users.
- Secure browsing using a SOCKS proxy.
Potential Risks
- Misconfiguration: Incorrect setup may expose sensitive services to the wrong audience.
- Security Implications: Open forwarding can introduce risks if access control isn’t tightly managed.
